Dynamic Threat Scoring: How It Works
Dynamic threat scoring assigns real-time risk scores (0–100) to users, devices, and applications based on behavior, context, and data from tools like SIEM, EDR, and network monitors. Unlike static models, it continuously updates scores to reflect changing conditions, helping security teams focus on high-risk threats. This system integrates internal telemetry (e.g., user activity, network flows) with external intelligence (e.g., CVE databases, threat tactics) for precise assessments. Key benefits include fewer false positives, faster response times, and better prioritization of alerts. It also supports automated actions, like isolating risky devices or revoking access, making it a critical tool for modern cybersecurity operations.
Key Points:
- Real-Time Updates: Scores adjust frequently (e.g., every 2 minutes) based on new data.
- Data Integration: Combines internal signals (e.g., login activity) with external threat intel.
- Behavioral Baselines: Learns normal patterns to identify anomalies.
- Automation: Triggers actions like credential revocation when thresholds are exceeded.
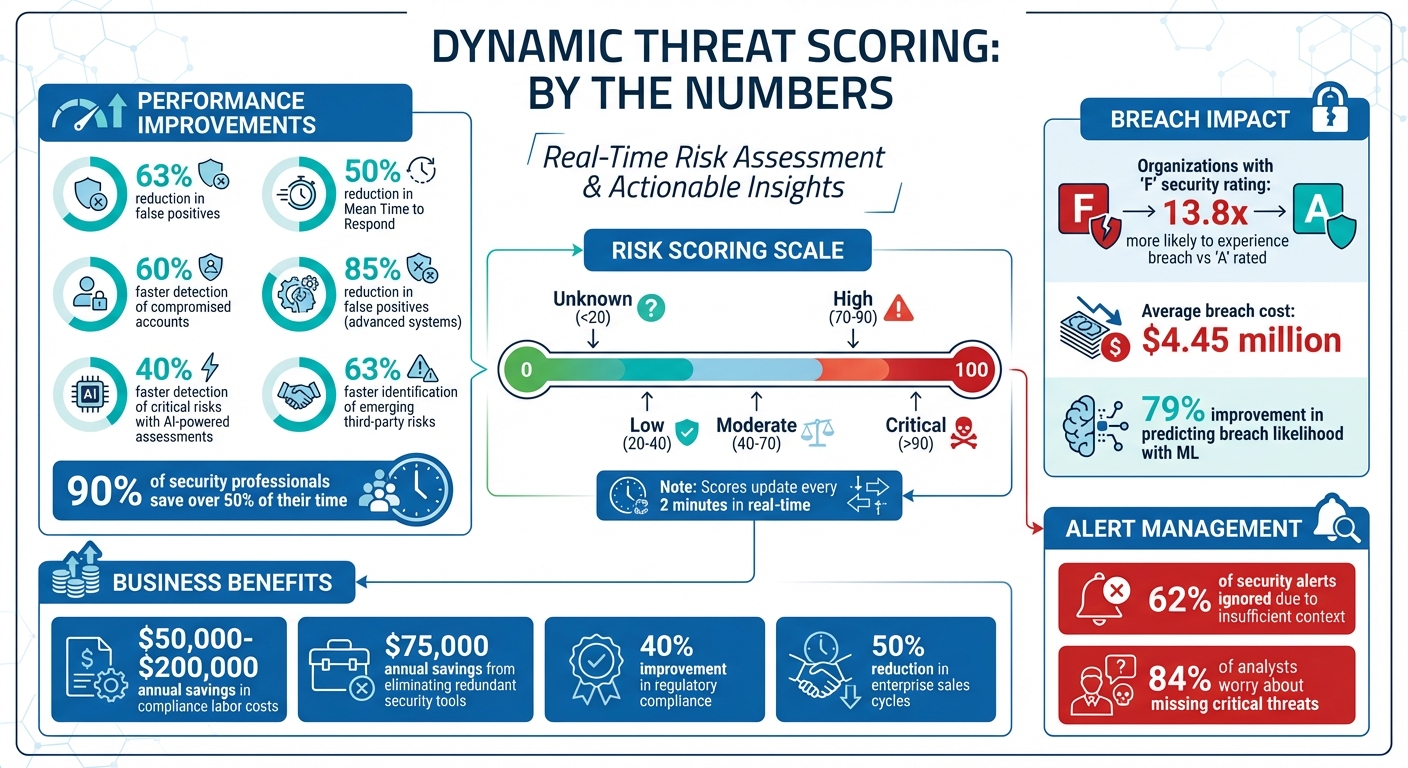
- Improved Efficiency: Cuts false positives by 63% and response times by 50%.
Dynamic threat scoring transforms security operations by enabling smarter, faster decisions and providing actionable insights for both analysts and executives.
Dynamic Threat Scoring Benefits and Impact Statistics
Core Components of Dynamic Threat Scoring Systems
Scoring Algorithms and Models
Dynamic threat scoring systems rely on a variety of algorithms to assess risks effectively. Machine learning models are adept at spotting anomalies by identifying deviations from typical patterns, while deep learning techniques process large volumes of data to uncover hidden threats. To make these outputs actionable, systems often use statistical functions, such as sigmoid curves, to convert raw data into a 0–100 risk scale for easier interpretation.
"In modern threat hunting, no single indicator can reliably flag suspicious activity… A composite scoring model addresses this limitation by transforming diverse behavioral telemetry into a structured framework", explains Manuel Arrieta, a Threat Hunter at Maveris.
Composite scoring models bring together various behavioral signals – like command-line entropy, process trees, and obfuscation markers – into a unified framework. These models also factor in asset criticality and user privileges, applying weighted adjustments to produce a normalized risk score. For instance, assets deemed "Extreme Impact" might receive a risk multiplier of 2.0, while "Low Impact" assets might only get 0.5. Similarly, actions involving privileged users can double the risk weight, significantly influencing the overall risk assessment.
Rule-based engines complement these models by providing a baseline for detecting known threat patterns. At the same time, dynamic models adjust severity levels in real time, ensuring the scoring system remains responsive and relevant. These algorithmic outputs are further enriched through the integration of internal telemetry and external threat intelligence, as discussed next.
Internal and External Signal Integration
Dynamic scoring systems synthesize data from two primary sources: internal telemetry and external threat intelligence. Internal telemetry – drawn from tools like SIEM, endpoint detection, identity management systems, and network flow monitoring – helps identify the "where" and "who" of potential threats. External sources, such as CVE exploit databases, attacker tactics and techniques (TTPs), and malware indicators, provide insights into the "what" and "how" of emerging threats.
The real strength of these systems lies in their ability to combine and contextualize these signals. Internal data is enriched with asset metadata (e.g., criticality, exposure), user roles, and geographic details to evaluate the operational impact of a threat. For example, an unusual login from a privileged administrator accessing production databases carries a much higher risk than the same activity from a contractor working in a test environment.
Statistics highlight the importance of robust scoring systems. Organizations with an "F" security rating are 13.8 times more likely to experience a data breach than those rated "A." In 2023, the average breach cost reached $4.45 million. SecurityScorecard improved the accuracy of predicting breach likelihood by 79% through machine learning, which fine-tuned the weighting of various risk factors. Once internal and external signals are integrated and contextualized, dynamic systems use behavioral baselines to refine risk assessments further.
Behavioral Baselines and Risk Adjustments
Behavioral baselines establish what "normal" looks like for users, devices, and applications. These baselines require an initial learning period – typically two to four weeks – during which the system observes routine patterns to minimize false positives. They operate on multiple levels, including individual entities, role-based peer groups, and organization-wide benchmarks.
These baselines are not static; they evolve automatically to accommodate changes such as role transitions, seasonal workload fluctuations, or infrastructure growth. For instance, Microsoft Sentinel employs the term frequency-inverse document frequency (TF-IDF) algorithm to rank anomalies within peer groups. Smaller peer groups are given higher anomaly weights, ensuring more precise risk assessments.
"Baselines evolve continuously, adapting to role changes, seasonal workloads, and infrastructure growth", notes Seceon.
This adaptive approach uses rolling baselines and statistical confidence intervals to distinguish legitimate workflow changes from malicious anomalies, refining the system’s ability to detect threats over time.
Benefits of Dynamic Threat Scoring Over Static Models
Limitations of Static Risk Scoring
Static risk scoring relies on fixed assumptions, assigning preset values without accounting for real-time behaviors or changing conditions. This lack of adaptability results in poor contextual understanding – treating events the same regardless of factors like asset importance or user privileges. It also fails to catch nuanced indicators, such as lateral movements or unusual access patterns.
This rigidity leads to operational challenges. For example, static models can’t differentiate between a routine login from a test environment and a privileged administrator accessing sensitive production databases. The numbers highlight the issue: about 62% of security alerts go ignored due to insufficient context or prioritization, and 84% of security analysts worry about missing critical threats amidst overwhelming data volumes.
Advantages of Dynamic Models
Dynamic models take a more adaptive approach by continuously updating risk scores as new data flows in from various sources. Unlike static systems that depend on periodic manual updates, dynamic systems refresh risk values in real time – sometimes as often as every two minutes – using data from SIEM logs, EDR alerts, IAM systems, and cloud security metrics.
This approach significantly improves outcomes. Dynamic scoring reduces false positives by 63% and cuts the Mean Time to Respond by 50%. Moreover, organizations utilizing these systems report up to a 40% reduction in financial losses tied to fraud. By correlating data from multiple sources, dynamic models create comprehensive risk snapshots that consider asset importance, user roles, and environmental factors.
Another key benefit is automation. When risk scores exceed set thresholds, dynamic systems can automatically initiate containment actions – like isolating devices, revoking credentials, or logging users out – without waiting for manual input. This real-time adaptability allows security teams to prioritize and act on threats as they emerge.
Impact on Security Teams
Dynamic threat scoring has revolutionized how security teams operate. A striking 90% of security professionals report saving over 50% of their time with these systems, enabling them to focus on high-priority threats and reduce triage backlogs.
"Dynamic risk scoring is no longer optional – it’s essential."
This statement underscores the urgency of aligning security operations with the fast pace of modern threats. Dynamic systems help organizations better allocate resources and respond to risks quickly. Additionally, aggregated risk scores provide CISOs with actionable insights into their organization’s overall risk posture, aiding in smarter security investments and compliance reporting.
Platforms like The Security Bulldog (https://securitybulldog.com) showcase how dynamic threat scoring can elevate threat detection and response, empowering security teams to act decisively when every second counts. These advantages pave the way for more effective security operations, setting the stage for the next steps in implementation.
How to Implement Dynamic Threat Scoring in Security Operations
Integration with Existing Tools
To implement dynamic threat scoring, start by gathering telemetry from tools like EDR, SIEM, identity providers, network analytics, and cloud security platforms. Enhance this raw data with metadata about asset importance, exposure levels, and user roles. This enriched data helps establish precise behavioral baselines. Once scoring is in place, integrate it into your existing security stack, enabling tools like SIEM, SOAR, and IAM systems to leverage real-time risk insights for better alerting, automated responses, and adaptive access control. Governance policies should define clear risk thresholds and enforcement triggers for actions such as credential revocation or device isolation.
To keep the scoring model effective, continuously refine it by feeding back labeled security outcomes. This feedback loop improves anomaly detection and minimizes false positives. Advanced systems, for example, process over 100 billion daily signals and 2 billion malware requests, leading to a 79% improvement in correlating security ratings with actual breach risks. A demonstration by The Security Bulldog (https://securitybulldog.com) illustrates how AI-driven analysis of open-source intelligence can deliver timely and accurate risk assessments. These integration steps lay the groundwork for stronger threat detection and faster automated responses.
Improving Threat Detection and Response
Dynamic threat scoring takes detection and response to the next level by assigning composite risk scores. These scores consider factors like event rarity, potential business impact, and the reputation of the threat source. This scoring system allows analysts to focus on high-risk entities and uncover stealthy behaviors that traditional signature-based methods might miss. For example, an unusual login attempt by a privileged administrator would generate a higher score compared to routine user logins.
Organizations adopting dynamic scoring can identify emerging third-party risks up to 63% faster than those using static models. Additionally, AI-powered risk assessments cut the time needed to detect critical risks by 40%. When risk scores surpass predefined thresholds, SOAR platforms can take immediate action – isolating devices, revoking credentials, or logging users out – without waiting for manual intervention.
Multi-Tenant and Data Segmentation Considerations
In complex environments, particularly multi-tenant setups, dynamic scoring requires customized and isolated models for each segment. For example, you might assign different weights to attributes like temporal relevance for IP addresses and persistent relevance for domains. Industry-specific configurations are also crucial: financial institutions need models that reflect threats specific to their sector, while government agencies require scoring tailored to their unique security challenges.
Accurate scoring depends on comprehensive telemetry from tools like EDR, SIEM, identity providers, and cloud workloads. This is especially important in multi-tenant environments, where each segment’s unique threat exposure and profile must be accurately represented in its scoring model. By tailoring these models to the specific needs of each segment, you ensure that dynamic scoring remains both precise and effective.
sbb-itb-9b7603c
Executive-Level Insights and Decision Support
Risk Dashboards and Aggregated Insights
Dynamic threat scoring takes raw security data and turns it into real-time insights that help CISOs and security leaders quickly evaluate organizational risks. Executives can view these risks through dynamic scales (like 0–100 or 0–1000). For example, scores exceeding a set threshold (e.g., above 850) for high-value assets signal critical risks. Elastic Security updates these scores hourly, analyzing data from the past 30 days and categorizing results into five clear risk levels: Unknown (<20), Low (20–40), Moderate (40–70), High (70–90), and Critical (>90).
These dashboards go beyond just technical risk assessments by factoring in business context, such as the importance of specific assets and their exposure to external threats. For instance, a production database exposed to the internet would be considered a higher risk than an internal test server, even if both have similar vulnerabilities. This added layer of context helps executives pinpoint the organization’s most vulnerable areas and evaluate how these risks could affect revenue, customer trust, or regulatory compliance. These insights play a vital role in shaping strategic security governance.
Data-Driven Security Governance
Dynamic scoring shifts security decision-making from relying on intuition to using solid, data-backed frameworks. By leveraging real-time scoring, CISOs can clearly show the board how security investments align with measurable risks, ensuring resources are allocated where they’ll have the greatest impact. This methodology supports Cyber Risk Quantification (CRQ), translating technical risks into financial terms – an essential tool for budget approvals and securing cyber insurance. Notably, 88% of board directors now consider cybersecurity a business issue, not just an IT concern, which underscores the need to communicate in terms that resonate with them.
Additionally, this scoring framework simplifies compliance reporting by providing clear, auditable evidence of risk-based decisions. For example, prioritizing the patching of a critical asset over a less valuable one can significantly improve regulatory compliance, with some organizations reporting a 40% improvement. Governance policies that set clear risk thresholds and include automated enforcement mechanisms further ensure consistent security practices across the board.
Business Benefits
These governance tools and actionable insights bring measurable financial and operational benefits. For example, dynamic threat scoring allows organizations to detect compromised accounts 60% faster and reduce false positives by 85%. This efficiency directly translates into cost savings. Automated compliance workflows can save between $50,000 and $200,000 annually in labor costs, while eliminating redundant security tools can cut licensing expenses by about $75,000 per year. Considering the average cost of a data breach exceeds $4.44 million, the return on investment is clear.
Beyond cost savings, dynamic scoring also accelerates revenue generation. By providing real-time security posture data, these systems streamline vendor assessments, cutting enterprise sales cycles by up to 50%. As Steve Zalewski, former CISO at Levi Strauss & Co., once put it:
"How does this help me sell more jeans?"
Conclusion
Key Takeaways
Dynamic threat scoring is transforming how security teams detect, prioritize, and respond to cyber threats. Unlike static models, it continuously evaluates risk based on real-time behavior, data from multiple sources, and the surrounding environment. By integrating information from SIEM, EDR, IAM, network, and cloud systems, it provides a constantly updated, all-encompassing view of risk.
The operational advantages are clear. Organizations leveraging dynamic scoring see fewer false positives, which helps reduce analyst burnout and clears up investigation backlogs. Advanced systems also deliver contextual prioritization, ensuring security teams focus on threats that pose real business risks. Consider this: companies with an "F" security rating are 13.8 times more likely to suffer a breach compared to those with an "A" rating. This underscores how critical dynamic scoring is for effective risk management.
But the benefits go beyond the security operations center. At the executive level, dynamic scoring translates technical risks into financial terms with Cyber Risk Quantification, allowing CISOs to justify investments and demonstrate ROI to the board. It also supports Zero Trust architectures by enabling automated, real-time access decisions based on current risk levels.
These advancements offer actionable insights to elevate your security strategy.
Next Steps
To start reaping the benefits, focus on high-priority areas like monitoring privileged accounts or securing critical production systems. Success depends on the quality of your data, so make sure your security stack is fueled by accurate, high-fidelity telemetry from endpoints, cloud environments, and identity providers. Tools like The Security Bulldog (https://securitybulldog.com) can give your threat intelligence efforts a boost. By leveraging AI-powered natural language processing, it simplifies open-source cyber intelligence, helping your team identify threats faster, make smarter decisions, and seamlessly integrate dynamic scoring into your workflows. Dynamic risk scoring isn’t just a nice-to-have anymore – it’s a must-have.
AI Powered Risk Scoring with Falcon Next-Gen SIEM
FAQs
How does dynamic threat scoring help reduce false positives?
Dynamic threat scoring takes a smarter approach to identifying risks by evaluating real-time contextual, behavioral, and situational factors instead of sticking to rigid rules or pre-set models. This shift allows security systems to better distinguish between actual threats and harmless irregularities.
By constantly adjusting risk levels in response to evolving threat conditions, it cuts down on excessive alerts that can bog down security teams. This means analysts can concentrate on real, high-priority threats, making decisions faster, simplifying investigations, and zeroing in on the most critical incidents with precision.
How do behavioral baselines contribute to dynamic threat scoring?
Behavioral baselines play a key role in dynamic threat scoring by defining what qualifies as normal activity for users or systems within a network. These baselines act as a reference point, enabling the system to spot unusual behaviors that might indicate a potential threat.
Take this example: if a user suddenly starts accessing sensitive files or performing activities that deviate from their usual patterns, the system can flag this as suspicious. This method adapts to the specific context, making threat detection more precise, cutting down on false alarms, and ensuring risk assessments happen in real time. By tailoring the analysis to individual behaviors, behavioral baselines make dynamic threat scoring a more effective tool for identifying cyber risks.
How does dynamic threat scoring help improve cybersecurity response times?
Dynamic threat scoring revolutionizes cybersecurity by delivering real-time assessments of potential risks. Unlike traditional static methods, this approach continuously evaluates data from assets, user behavior, and activities, adjusting as conditions evolve. The result? Security teams can quickly zero in on high-risk threats and cut down on wasted time dealing with false alarms or low-priority issues.
By blending threat intelligence with operational data, dynamic threat scoring produces precise, actionable insights that align with the ever-changing threat landscape. This streamlined process empowers organizations to detect, contain, and address incidents faster, ensuring resources are directed where they’re needed most. It’s an efficient way to strengthen security and stay ahead of potential breaches.