The Benefits of Integrating CrowdStrike and The Security Bulldog
Cybersecurity threats are evolving fast. Attackers can breach systems in just 51 seconds, and malware-free attacks now account for 81% of intrusions. To stay ahead, integrating CrowdStrike Falcon and The Security Bulldog offers a powerful solution.
Here’s what you gain:
- Fewer alerts, more accuracy: 98% of alerts are true positives, with a 500x reduction in noise.
- Time saved: Automating threat research saves 11,000 hours annually.
- Lower costs: Organizations report saving up to $3M in security expenses.
- Faster response: Tasks like endpoint isolation and credential resets happen instantly.
This integration combines CrowdStrike’s real-time endpoint protection with The Security Bulldog’s AI-driven threat intelligence. Together, they deliver precise detection, automated workflows, and smarter vulnerability management – all in one system.
If your team struggles with alert fatigue, slow responses, or manual research, this partnership can simplify operations and improve results.
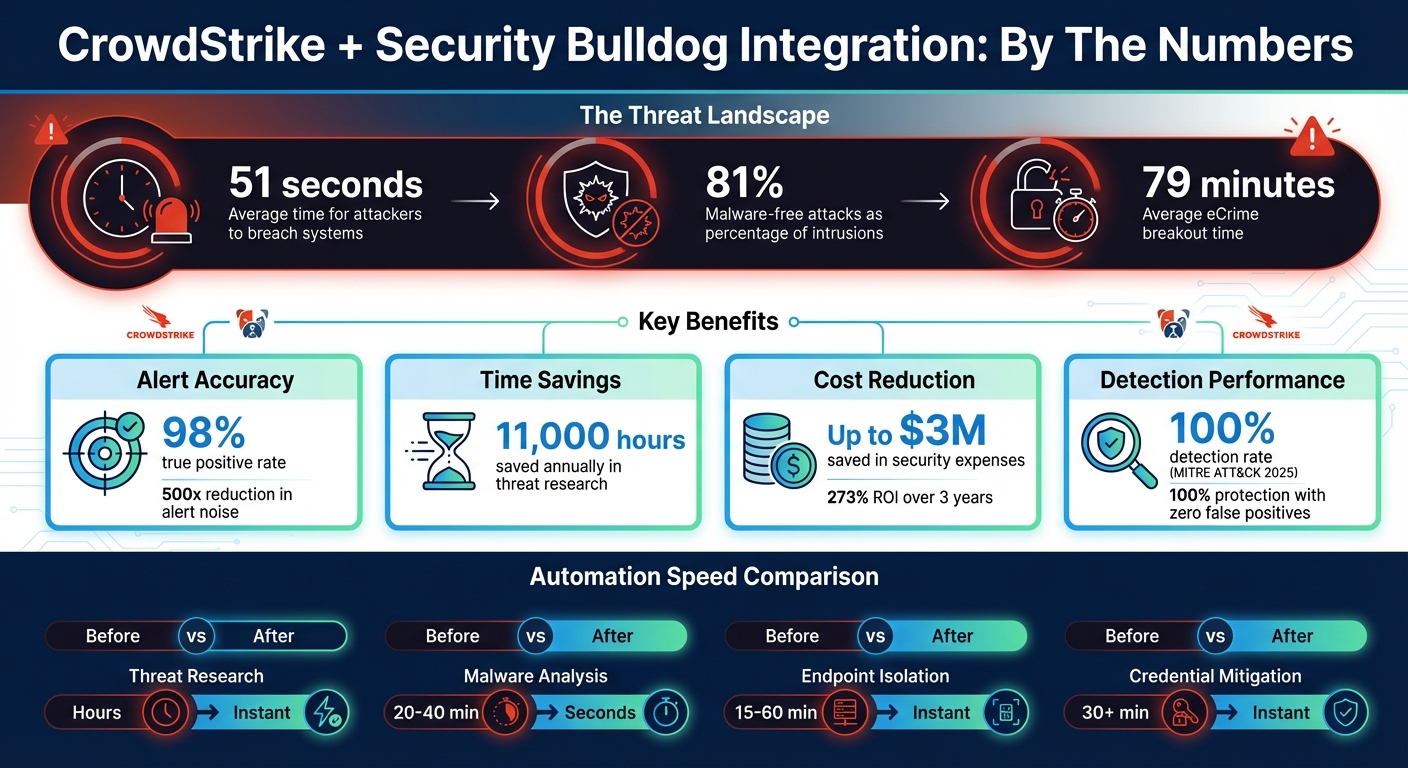
CrowdStrike and Security Bulldog Integration: Key Benefits and ROI Statistics
How to Defend Against Threats with Falcon Intelligence
Improved Threat Detection and Intelligence
When CrowdStrike’s endpoint protection teams up with The Security Bulldog’s AI-driven OSINT tools, security teams get an integrated, context-rich solution. CrowdStrike’s Signal AI Engine develops behavioral models for each host, identifying anomalies that traditional, signature-based systems might overlook. Meanwhile, The Security Bulldog enhances these findings by pulling in external intelligence from sources like MITRE ATT&CK, CVE databases, criminal forums, and the dark web. This combination links internal alerts to broader global threat patterns and adversary tactics. The result? A more streamlined and focused detection process.
This collaboration isn’t just about better detection; it also dramatically cuts through the noise in security operations. By correlating endpoint data with real-time OSINT, irrelevant alerts are filtered out, leaving analysts to concentrate on threats that genuinely matter. Organizations adopting this approach have reported a 500x reduction in alert volumes, with 98% of the remaining alerts being true positives.
Speed is critical when adversaries can infiltrate systems in as little as 51 seconds. Manual research simply can’t keep up. With this integration, intelligence gathering is automated, freeing up security teams from time-consuming tasks. On average, this saves teams around 11,000 hours annually in threat research time.
"CrowdStrike doesn’t just give us intel, they give us understanding, they help us identify specific activity, map it to threat actors, and respond based on what those actors were known to do."
- Olivier Minkowski, Senior Insider Threat Lead, ServiceNow
| Feature | Standalone Endpoint Protection | Standalone AI OSINT | Integrated Precision |
|---|---|---|---|
| Detection Basis | Internal telemetry and known signatures | External web, dark web, and social data | Correlated internal/external behavioral analysis |
| Alert Accuracy | Higher potential for false positives | Broad context but lacks internal link | 98% true positive rate; 500x reduction in noise |
| Research Effort | Manual investigation of each alert | Manual correlation with internal logs | 11,000 hours saved via automated research |
| Response Speed | Reactive to endpoint activity | Proactive but requires manual execution | Automated, agentic response (e.g., blocking IPs/domains) |
Automated Workflow Processes
Security analysts often manage between 40 and 70 tools, constantly switching screens in a frustrating process dubbed "swivel-chair syndrome". This disjointed method not only slows response times but also contributes to analyst burnout and costly mistakes. When the average eCrime breakout time is just 79 minutes and attackers exploit vulnerabilities in seconds, this inefficiency becomes a critical issue. It’s clear why automation is becoming essential in security operations.
To address these challenges, integrating CrowdStrike with The Security Bulldog streamlines operations by automating intelligence gathering and response coordination. This integration builds on the enhanced threat detection capabilities discussed earlier, delivering real-time intelligence directly into detections. The result? Analysts no longer need to waste time on manual research or switching between tools. CrowdStrike’s Falcon Fusion offers native SOAR (Security Orchestration, Automation, and Response) capabilities through a no-code interface, allowing teams to design intricate workflows in minutes instead of days. With over 61,000 workflow definitions available, tasks like phishing analysis and endpoint isolation become automated and efficient.
The benefits are undeniable. Automated playbooks now handle tasks – like isolating endpoints, blocking malicious IPs, or resetting credentials – in mere seconds. Previously, these actions could take up to an hour. Even credential protection is fully automated: when compromised passwords appear on criminal forums, the system enforces password resets or activates multi-factor authentication without requiring human input.
| Workflow Task | Manual Process Time | Automated Process Time |
|---|---|---|
| Threat Research & Enrichment | Hours of manual searching | Real-time / Instantaneous |
| Malware Analysis | 20–40 minutes per file | Machine speed / Seconds |
| Endpoint Isolation | 15–60 minutes (detection to action) | Instant upon trigger |
| Credential Mitigation | 30+ minutes (manual reset/MFA) | Automated / Instant |
"Attackers use automation – and your team should too."
- Paola Miranda, Next-Gen SIEM & Log Management, CrowdStrike
sbb-itb-9b7603c
Better Vulnerability Management
By combining automated workflows with CrowdStrike’s internal telemetry and The Security Bulldog’s external intelligence, vulnerability management becomes more streamlined and effective. This integration uses CrowdStrike Falcon’s Context Enrichment feature to bring external intelligence directly into the Falcon console. Security teams no longer have to guess which vulnerabilities demand immediate attention – they can now see real-time exploit trends and technical analysis alongside CrowdStrike’s ExPRT (Exploit Prediction Rating) scores. This approach not only identifies vulnerability risks but also enables focused and efficient remediation efforts.
This consolidated view simplifies the process of prioritizing remediation. Instead of relying solely on CVSS scores, analysts benefit from a multi-dimensional scoring model that blends technical risk with the urgency of real-world threats.
The practical advantages are evident in everyday workflows. Administrators can activate Context Enrichment through the CrowdStrike Store and use Falcon’s Global Search to access enriched data directly within the console. This eliminates the need to switch between platforms. Additionally, these scores can be seamlessly integrated into Falcon Fusion SOAR playbooks, enabling automated, risk-based remediation.
Here’s a breakdown of the key benefits of this integrated approach:
| Feature | CrowdStrike Falcon (Individual) | The Security Bulldog (Individual) | Integrated Benefit |
|---|---|---|---|
| Vulnerability Data | Internal asset telemetry and CVE detection | External exploit trends and aggregated security news | Real-time mapping of internal vulnerabilities to active external threats |
| Scoring Model | ExPRT based on technical risk | Sentiment and trending scores from external analysis | Combined scoring (Technical Risk + Real-world Urgency) |
| Workflow | Endpoint-focused detection and response | Research-driven analysis | Unified console triage; less platform switching |
| Remediation | Manual or policy-based patching | Advisory-driven prioritization | Automated, risk-aware patching informed by external intelligence |
"Having a partner that can help you dig in and really investigate and have that threat intelligence to back it up… has definitely helped. I can take a deep breath."
- Kelly McCracken, SVP of Detection and Response at Salesforce
Pros and Cons
Integrating CrowdStrike with The Security Bulldog brings notable improvements in threat detection and response speed. During the 2025 MITRE ATT&CK Enterprise Evaluations, CrowdStrike demonstrated a 100% detection rate and 100% protection with zero false positives, showcasing its reliability. Organizations using the platform reported an impressive 273% ROI over three years, making it a cost-effective solution. The integration shines in automating threat intelligence workflows, reducing detection times, and providing a unified view of threats across endpoints and cloud environments. Additionally, it automates response playbooks, streamlining operations.
That said, some challenges persist. Integrating with newer applications may require extra configuration, Linux support is less than ideal, and the absence of a no-code plugin system makes creating custom workflows more technical. Furthermore, uninstalling the sensor can be cumbersome due to the need for API token retrieval.
| Aspect | Advantages | Limitations |
|---|---|---|
| Detection & Response | Real-time intelligence enrichment; 100% detection rate in MITRE evaluations | Integration with newer applications may demand additional configuration |
| Workflow Automation | Custom playbooks for automating tasks like endpoint isolation and IP blocking | No no-code plugin system; technical expertise needed for custom workflows |
| Visibility | Unified view across endpoint, identity, cloud, and third-party data sources | Linux support requires improvement |
| Cost Efficiency | 273% ROI over three years; Falcon Flex consumption model offers financial flexibility | None |
| Operational Management | Automated malware sandboxing and credential protection | Sensor uninstallation can be time-consuming due to API token retrieval |
For those considering the platform, CrowdStrike offers a 15-day free trial and the flexible Falcon Flex financing model, allowing organizations to test the system before committing fully. Additionally, for teams with limited internal resources, CrowdStrike’s Managed Detection and Response (MDR) service provides operational support without the need to expand headcount.
Conclusion
Pairing CrowdStrike with The Security Bulldog transforms how organizations handle cybersecurity. By integrating enriched threat intelligence directly into the Falcon interface, analysts can work more efficiently without switching between tools. This seamless setup has already shown its worth in actual deployments, cutting down alert volumes significantly while maintaining precision in threat detection. It’s a solution that not only sharpens detection capabilities but also simplifies day-to-day operations.
The benefits extend beyond just operational improvements. Many organizations have reported saving both time and money thanks to automated workflows and smarter threat prioritization. With The Security Bulldog’s AI-driven insights, teams can access curated threat data faster, enabling quicker and more informed responses.
For teams overwhelmed by alert fatigue, limited resources, or slow triage processes, this integration offers a practical and effective solution. A 15-day free trial allows teams to explore these capabilities risk-free. By activating context enrichment applications through the CrowdStrike Store, security teams can immediately start using automated playbooks to reduce manual effort and focus on what matters most.
If your goal is to cut investigation times, strengthen your security posture, and make faster, better-informed decisions, this integration delivers measurable results. The combination of CrowdStrike’s proven 100% detection rate and The Security Bulldog’s AI-powered intelligence creates a robust, efficient defense system that’s ready to tackle today’s cybersecurity challenges.
FAQs
How does integrating CrowdStrike with The Security Bulldog help reduce alert fatigue?
Integrating CrowdStrike with The Security Bulldog simplifies threat management by automating threat intelligence processes. This reduces false positives and ensures that critical alerts are prioritized, helping security teams concentrate on real threats instead of getting bogged down by irrelevant notifications.
By refining workflows and improving the precision of threat detection, this integration boosts efficiency. It equips teams to respond swiftly and effectively to potential risks, reinforcing cybersecurity defenses across the board.
How does integrating CrowdStrike with The Security Bulldog help organizations save money?
Integrating CrowdStrike with The Security Bulldog can help organizations save both time and money by automating essential cybersecurity tasks. Processes like alert triage, vulnerability prioritization, and indicator enrichment are handled automatically, cutting down on the manual effort required. This not only reduces labor costs but also frees up security teams to focus on more strategic, high-priority activities.
On top of that, the integration improves the accuracy of threat detection using AI-driven tools. This means fewer false positives and a lower chance of overlooking real threats, which can be costly if left unaddressed. Preventing incidents before they escalate helps organizations avoid expenses tied to remediation, system downtime, and potential damage to their reputation. In short, this collaboration streamlines security operations while boosting protection and reducing costs.
How does integrating CrowdStrike with The Security Bulldog improve vulnerability management?
Integrating CrowdStrike with The Security Bulldog takes vulnerability management to the next level by blending AI-driven automation with cutting-edge threat intelligence. This partnership enables security teams to swiftly pinpoint, prioritize, and tackle vulnerabilities, all while cutting down on manual tasks and reducing the chance of human error.
With features like real-time detection, automated workflows, and actionable insights, teams can zero in on the most pressing risks, considering factors such as asset value and the likelihood of exploitation. By simplifying these processes, organizations can address vulnerabilities more efficiently and stay ahead of evolving threats, including zero-day exploits, bolstering their overall cybersecurity defenses.