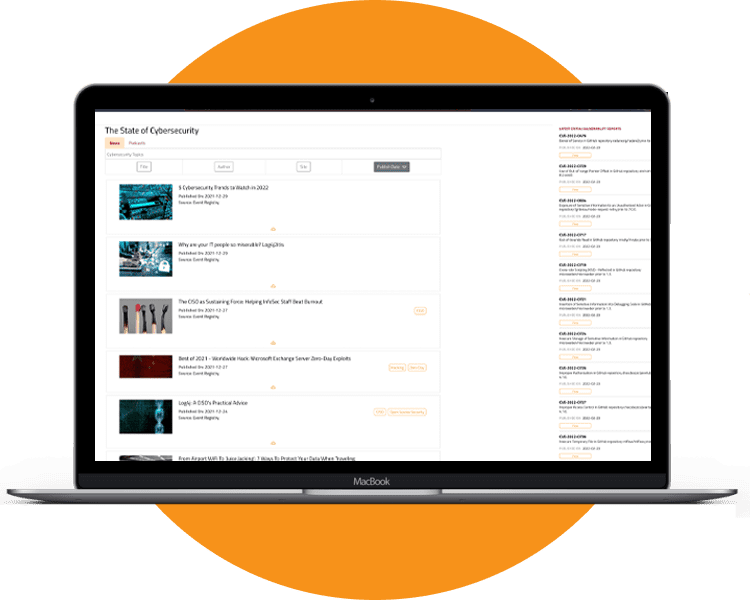
Posts Tagged ‘The Security Bulldog’
NLP in Cybersecurity: Contextual Threat Analysis
Explore how NLP enhances cybersecurity through advanced threat detection, automated analysis, and improved operational efficiency.
Read MoreAI vs. Manual Threat Intelligence Sharing
Explore the differences between AI-powered and manual threat intelligence sharing, focusing on speed, accuracy, and the importance of human expertise.
Read MoreAnnouncing the Integration of the Known Exploited Vulnerabilities (KEV) Database into The Security Bulldog’s AI Engine
In today’s rapidly evolving cyber threat landscape, speed and precision are everything. Security teams are bombarded with thousands of vulnerabilities every week, but not all pose the same risk. That’s why The Security Bulldog is proud to announce the integration of the CISA Known Exploited Vulnerabilities (KEV) database into our AI-powered cybersecurity intelligence platform- a…
Read MoreAnnouncing Automated Email Alerts: The Next Leap in Proactive Cybersecurity
Today’s cyber threats move fast-so your security intelligence should move even faster. That’s why The Security Bulldog is excited to announce our new Automated Email Alert feature, designed to keep enterprise security teams instantly informed about critical vulnerabilities, threats, and actionable intelligence, right in their inbox. This new capability is more than just a notification system-it’s a…
Read MoreCyber Pro Podcast Holistic Cybersecurity Approach and Strategy with Jeff Majka
Jeff Majka emphasized the importance of a holistic approach to cybersecurity, focusing on the roles and operations of human beings rather than just the deployment of tools. He argued that cybersecurity is a human problem, and human nature must be considered when seeking solutions. Jeff also highlighted the need for a robust cybersecurity strategy that…
Read MoreCISO Tradecraft Podcast- 178 – Cyber Threat Intelligence with Jeff Majka & Andrew Dutton
In this episode of CISO Tradecraft, hosts G Mark Hardy and guests Jeff Majka and Andrew Dutton discuss the vital role of cyber threat intelligence in cybersecurity. They explore how Security Bulldog’s AI-powered platform helps enterprise cybersecurity teams efficiently remediate vulnerabilities by processing vast quantities of data, thereby saving time and enhancing productivity. The conversation…
Read MoreEnhancing Productivity and Accelerating Remediation: The Power of OSINT
In today’s rapidly evolving digital landscape, the ability to swiftly gather accurate and relevant information is crucial for maintaining security and staying ahead of potential threats. This is where OSINT (Open Source Intelligence) comes into play, emerging as a pivotal tool in improving productivity and expediting the time it takes to address vulnerabilities. In this…
Read MoreTop 10 Resources for Learning Artificial Intelligence and Machine Learning in Cybersecurity
Artificial intelligence (AI) and machine learning (ML) are revolutionizing the field of cybersecurity. With the increasing complexity and frequency of cyber threats, organizations are turning to AI and ML to bolster their defense strategies. Whether you’re a cybersecurity professional or an aspiring enthusiast, staying updated with the latest advancements in AI and ML is crucial.…
Read MoreSpeed Up Remediation of CVE-2023-27350
Cybersecurity practitioners face the daunting task of keeping up with the latest vulnerabilities and exploits that constantly threaten the security of their organization’s networks and systems. The process of identifying and remediating vulnerabilities can be time-consuming, complex, and costly. However, with the advent of AI-powered cybersecurity intelligence platforms like The Security Bulldog, organizations can speed…
Read MoreThe Importance of Machine Learning in Cybersecurity: The Security Bulldog, Metasploit, Wireshark and nmap
In today’s fast-paced and constantly evolving digital world, cyber threats are a significant concern for both individuals and organizations. It is essential to have a robust cybersecurity infrastructure in place to protect against these threats and minimize the damage they can cause. This article will discuss The Security Bulldog, a machine learning cybersecurity intelligence platform,…
Read More